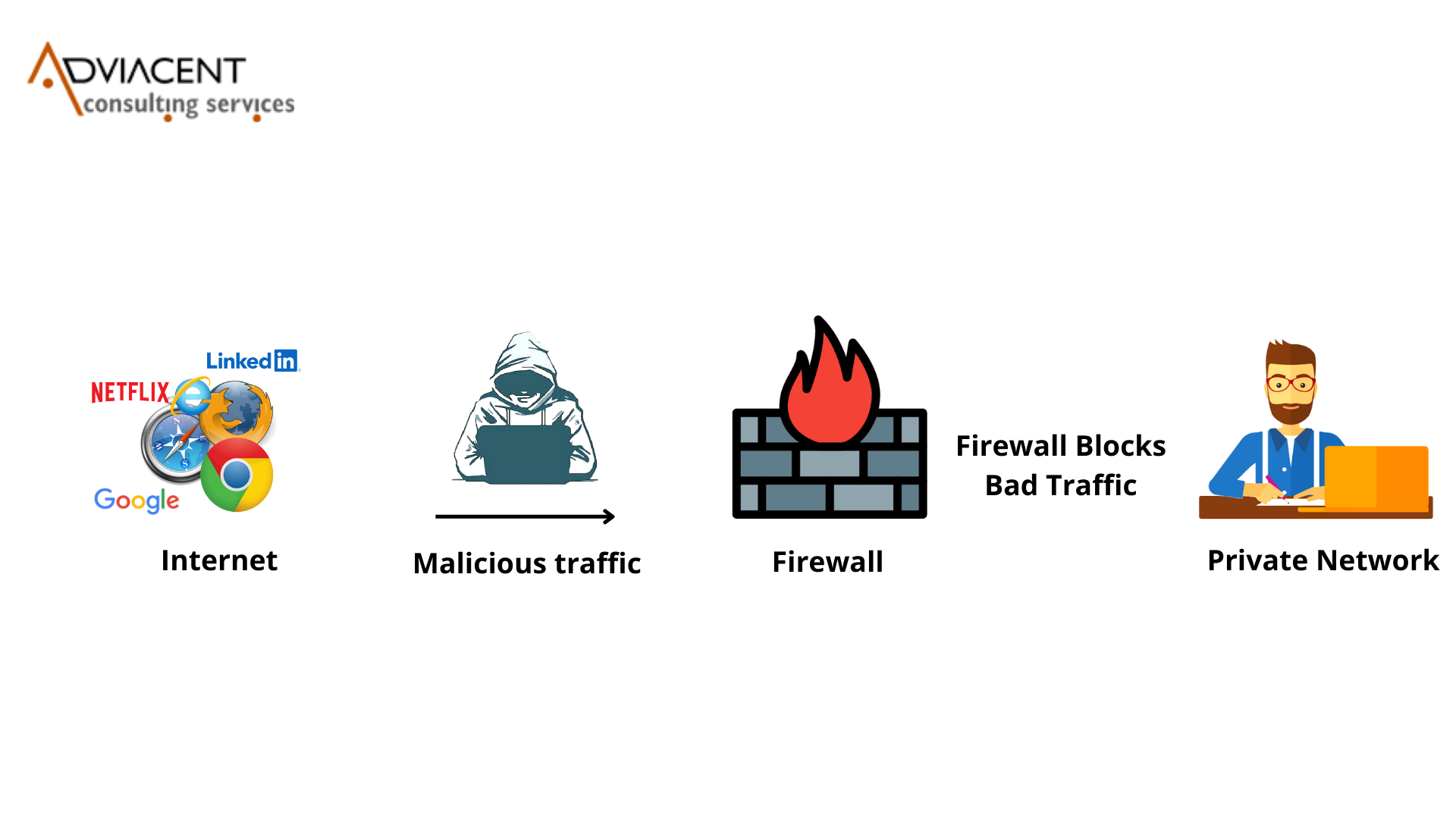
Internet is something that everyone needs, however accessing it isn’t as secure as we think. It always carries potential threats with it.
A computer must connect to the Internet to access websites on the web and this connectivity with the outside world can allow hackers to infect a host computer and get started with DDoS attacks when they connect to another machine.
This is where a firewall helps us to deal with such situations, but it’s of no use if it is not securely configured enough. We will discuss ways to make it more secure in this blog.
What is a Firewall?
Firewall, the name itself elaborates what it means. It is kind of security software which inhibits or prevents unauthorized network access or system access. It serves to the house wall which inhibits the thieves to enter the house. It works exactly the same as a house wall does. It controls the incoming and outgoing traffic, providing network security to your PC.
How does a Firewall work?
A firewall is a filter between two networks, the “filter” monitors data packet traffic incoming from a network and sometimes outgoing to a network. Checking IP addresses, Ports, and Protocols to determine if data traffic is allowed to travel to its intended destination. If an “accept” rule is not found or if a “deny” rule is found then traffic is prohibited from traveling to the intended destination.
If any incoming data fails to meet the defined security criteria, it will be rejected by the network firewall. Users have to configure a firewall according to the work they want it to perform. With proper configuration, you can prevent any unwanted viruses, hackers, or any other malicious program to enter your network.
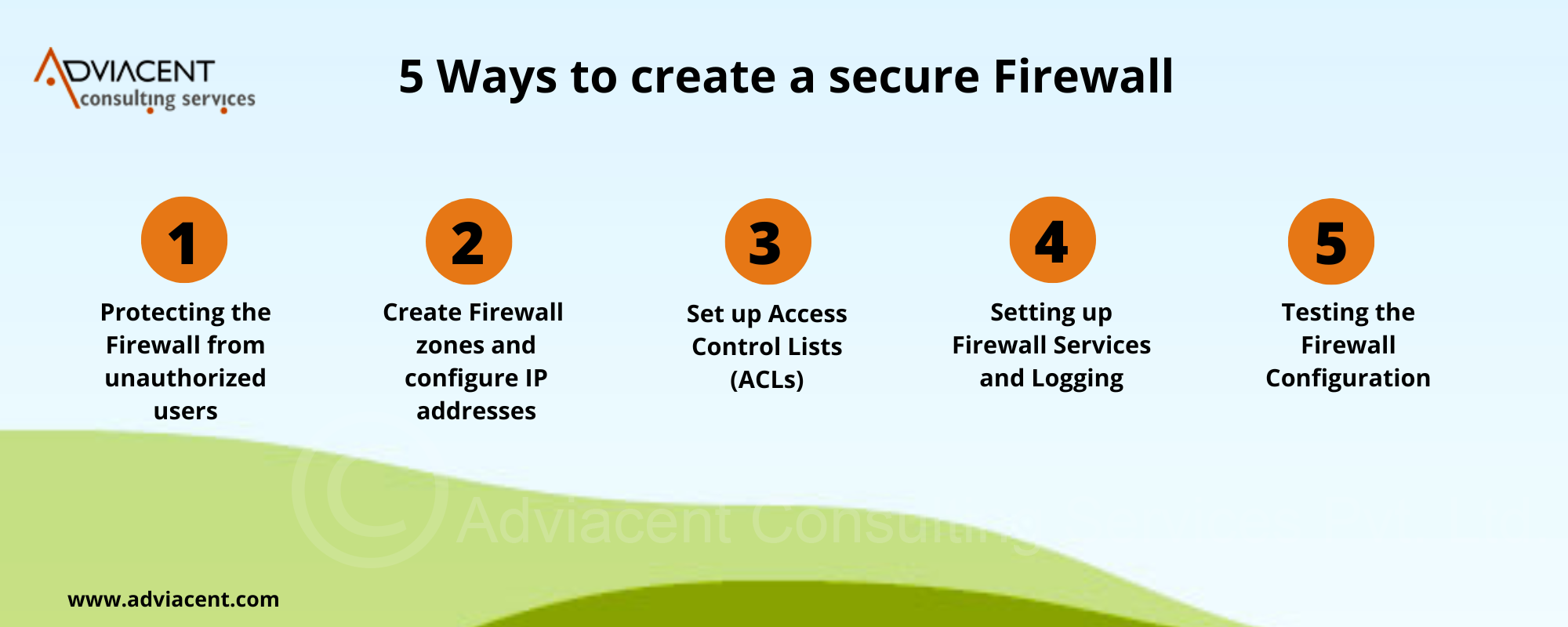
Ways to create a secure Firewall
-
Protecting the Firewall from unauthorized users
Update your firewall software to the latest version and ensure its default settings are updated.
Don’t use shared accounts that have multiple admins.
Ensure you don’t use any default accounts and create unique and complex passwords for each account.
Follow a proper configuration process. Creating a firewall without the proper configurations is like building a house without planning.
Always have an official request system to make changes in the firewall, It is not a good idea to make firewall changes through email, messaging, or verbal requests.
-
Create firewall zones and configure IP addresses
Identify and group the assets in your network (for example, credit card data or customer data). Then map them out so they can be grouped together and assigned to different networks or zones based on their functions and sensitivity levels.
The more zones you set up, the safer your network will be. This makes it easier to manage different types of network traffic. Multiple firewall zones can also be used to allow different types of traffic to flow through each zone separately.
-
Set up Access Control Lists (ACLs)
ACLs are a way to limit the number of devices that can connect to the network. Each ACL should include a “Deny All” rule, which means that all traffic will be denied. If a user enters the zone through one or more sub interfaces, then that user must first be authenticated and authorized before they can connect to their account. To ensure security, each ACL should also include an “Allow All” rule, which allows all IP addresses on the network to access data in that zone.
-
Setting up Firewall Services and Logging
Firewalls offer many services, such as intrusion prevention systems (IPS), network time protocol (NTP) servers, and more. It’s important to stop running any firewall-supported services that aren’t in use.
-
Testing the Firewall Setup
Once you’re certain your firewall settings are accurate, it is vitally important to test them. For the firewall to operate as intended and to ensure that the right traffic is allowed to pass, testing such as Vulnerability Assessment and Penetration Testing (VAPT) is essential. Make a backup in case the firewall setup fails while being tested.
What is VAPT?
Penetration Testing is a type of ethical hacking that tests the security of your organization’s network. It is also known as white hat hacking. This means that the goal of this type of testing is to help organizations improve their security without compromising their systems or users.
Penetration testing involves identifying, prioritizing and quantifying the threats within the network. It also includes checking the control of security, and evaluating the defenses against network-based attacks such as brute-force attacks, port scanning among others.
How Adviacent can help you with VAPT and firewall audit?
As affiliated with Cert-in impaneled cybersecurity solution firms, we help organizations provide secure access to their data and critical assets by employing the latest technology with our complete suite of VAPT services. Because of our strong expertise and experience in the field, Adviacent has formed a trusted relationship with CERT-In, allowing us to offer tailor-made, quality service to our clients across India.
Adviacent’s Firewall Audit provides insight into how your organization is using the firewall, which allows you to improve security posture and reduce risk exposure.
The Firewall Auditing process can be broken down into three major steps:
1) Identifying the firewalls to be audited
2) Planning for the audit
3) Executing the audit
Firewalls are frequently brought down by poorly configured applications and misconfigured services that are not updated on a regular basis.
We use industry-standard security tools such as Burpsuite, Nmap, and Metasploit and ensure that the firewall is configured properly, using the latest updates and patches, and discover any weak points that might exist within the infrastructure.
Tell us what kinds of configuration options you’d like to see for a firewall in the comments section below!

Vivek Kumar
Cybersecurity Enthusiast
A cybersecurity enthusiast helping businesses with their cyber-risks & understand the growing cyber threats.
I write about the latest news, review products and services on cybersecurity, and do a bit of podcasting.
I hope you enjoyed this post! If you have any suggestions, please leave a comment below.